Cryptography basics
Content
- Preamble
- symmetric encryption
- Asymertric encryption
- Hash functions
- Digital signature
- Protocols
- Digital certificates
- Common usages
Preamble
Who are Alice and Bob?
Alice and Bob are fictional characters used in cryptography to illustrate scenarios (source : Wikipedia).
The main characters are the following:
- Alice: the sender
- Bob: the recipient
- Eve: passive attacker (listens to conversations)
- Mallory: active attacker (listens, modifies or impersonates conversations)
Notation
| Notation | Description |
|---|---|
| $$ K_s $$ | Secret/Shared key |
| $$ K_{priv}^X $$ | X’s private key |
| $$ K_{pub}^X $$ | X’s public key |
| $$ E(K,M) $$ | Encrypt message M with key K |
| $$ D(K,C) $$ | Decrypt cipher C with key K |
| $$ S(K,M) $$ | Sign message M with key K |
| $$ V(K,M) $$ | Verify that M is signed with private key associated with key K |
| $$ h(X) $$ | Hash of X |
| $$ N_x $$ | Nonce (unique random number), x represents the instance |
Symmetric encryption
The simplest way to share data securely is using symmetric encryption (e.g. AES). In this scenario, Alice and Bob agreed on a share key $$ K_s $$ beforehand and then encrypt the messages with it. All messages are encrypted with the same key.
Basic protocol
- Alice and Bob agreed on a shared key $$ K_s $$ using an already secured and authenticated channel
- Alice encrypts plain text $$ M $$ as $$ E(K_s,M) \to C $$
- Alice sends cipher $$ C $$ to Bob
- Bob decrypts cipher as $$ D(K_s,C) \to M $$
Limitations
- Alice and Bob have a secured and authenticated channel to share keys
- If $$ K_s $$ is leaked, Eve can decrypt all the conversations in live or afterward and Mallory can create new messages
- Mallory can replay some messages after being sent by Alice or Bob. This can be mitigated by using nonce to authenticate messages (first nonce sent by Alice on a secured and authenticated channel)
Asymmetric encryption
Asymmetric encryption (e.g. RSA) removes the need for a secure channel as a prerequisite for the conversation as it uses a publicly shareable key $$ K_{pub} $$ to encrypt data and a private key $$ K_{priv} $$ to decrypt data.
Basic protocol
- Alice and Bob share their public keys $$ K_{pub}^{Alice} $$ and $$ K_{pub}^{Bob} $$ on a public channel
- Alice encrypts plain text $$ M $$ as $$ E(K_{pub}^{Bob},M) \to C $$
- Alice sends cipher $$ C $$ to Bob
- Bob decrypts cipher as $$ D(K_{priv}^{Bob},C) \to M $$
Limitations
- Mallory can replay some messages after being sent by Alice or Bob, this can be mitigated by using nonce to authenticate messages (first non send by Alice on a secured and authenticated channel)
- Asymmetric encryption algorithms consume more resources than symmetric encryption ones
Hash functions
Hash functions $$ h(X) $$ (e.g. SHA)) are used to convert data of any length to a fixed length data. This operation cannot be undone by design. Plain text cannot be retrieved from hash (note: some implementations are weak, so input can be retrieved and it is possible to find multiple values for the same hash). Hash functions are used to check data integrity and in authentication processes.
Basic protocol
- Alice and Bob agreed on a nonce $$ N_0 $$ using an already secured and authenticated channel
- Alice hash plain text $$ M $$ and nonce $$ N_0 $$ as $$ h(M,N_0) \to H_{MN_0} $$
- Alice send plain text $$ M $$ and hash to Bob $$ H_{MN_0} $$ to Bob
- Bob hash received plain text $$ M_r $$ and nonce $$ N_0 $$ as $$ h(M_r,N_0) \to H_{M_rN_0} $$ and compare it to received hash from Alice
- If $$ H_{M_rN_0} = H_{MN_0} $$ then, this means that message $$ M_r $$ is equal to $$ M $$ and so is from Alice (the message is authenticated).
Limitations
- Alice and Bob have a secured and authenticated channel to share first nonce
- In this example, nothing is encrypted and so Eve can read everything
Digital signature
Digital signature (e.g. RSA) are used to authenticate data using asymmetric encryption keys without any authenticated channel as a prerequisite of the conversation. The sender signs data using his own private key $$ K_{priv} $$ (the data hash is signed instead of the full data), and the recipient authenticates the data received using the sender’s public key $$ K_{pub} $$.
Basic protocol
- Alice sends message $$ M $$ with signature $$ S(K_{priv}^{Alice},h(L)) $$ to Bob
- Bob receives message $$ M_r $$ and verifies that it is signed with Alice’s private key using a verification algorithm as $$ V(K_{pub}^{Alice},h(M_r) $$. If $$ V $$ returns true, then this means that message $$ M_r $$ is equal to $$ M $$ and so is from Alice (the message is authenticated).
Limitations
- Mallory can replay messages
- In this example, nothing is encrypted and so Eve can read everything
- Bob has to make sure that $$ K_{pub}^{Alice} $$ is really owned by Alice and not by Mallory
Protocols
Cryptographic protocols (e.g. TLS wrapp-up all the above systems to create secured and authenticated channel, they have to prevent the following attacks types (not exhaustive):
- Read (live and after session)
- Replay
- Modification
- Repudiation
- Impersonation
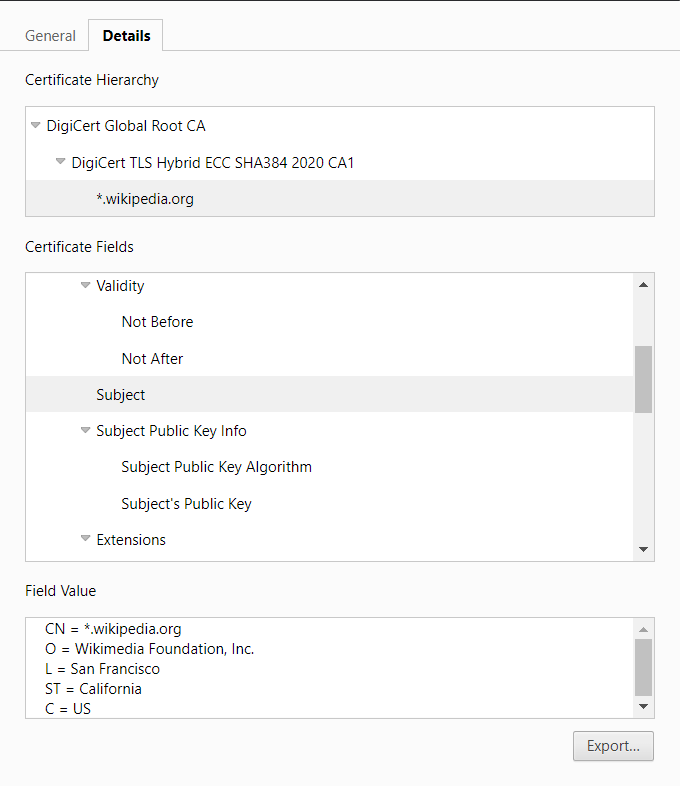
Digital certificates (aka public key certificates)
Digital certificates (e.g. x509 certificates) aim to authenticate public keys with a trust chain system (each certificate is signed by an ‘issuer’ until reaching certification authority signature which must be trusted by devices/users). A digital certificate contains multiple fields including public key, common name of the public key owner, serial number, validity and issuer identity (see example below).
Common usages
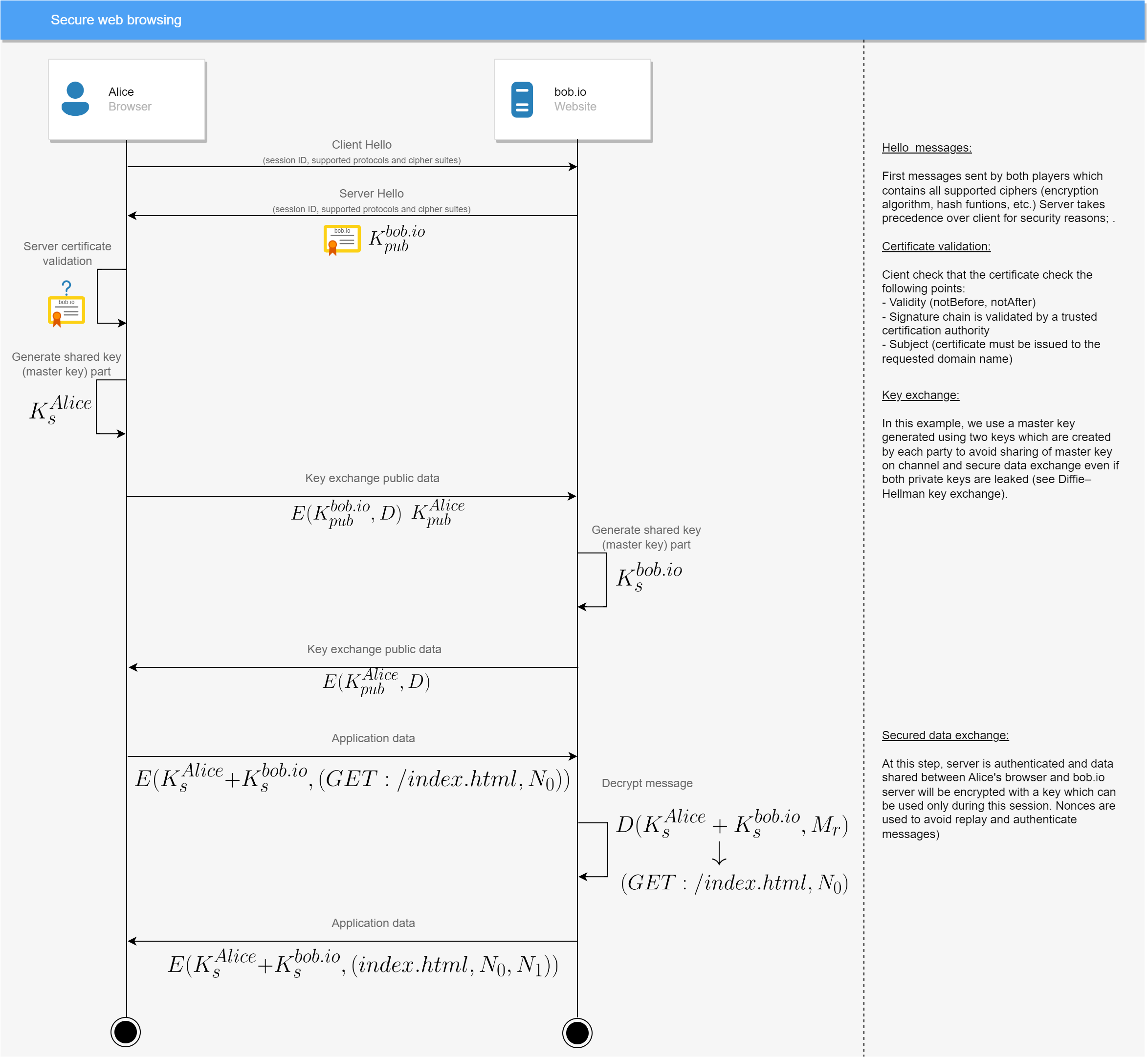
Secure web browsing
Scenario
Alice navigates to a website bob.io using HTTPS and so her browser authenticates server and encrypts data.
Prerequisites
bob.iomust have a public trusted certificate (i.e. signed by a certificate authority which is shipped with OS) or Alice must trustbob.iocertificate authority (e.g. for intranet).
Diagram
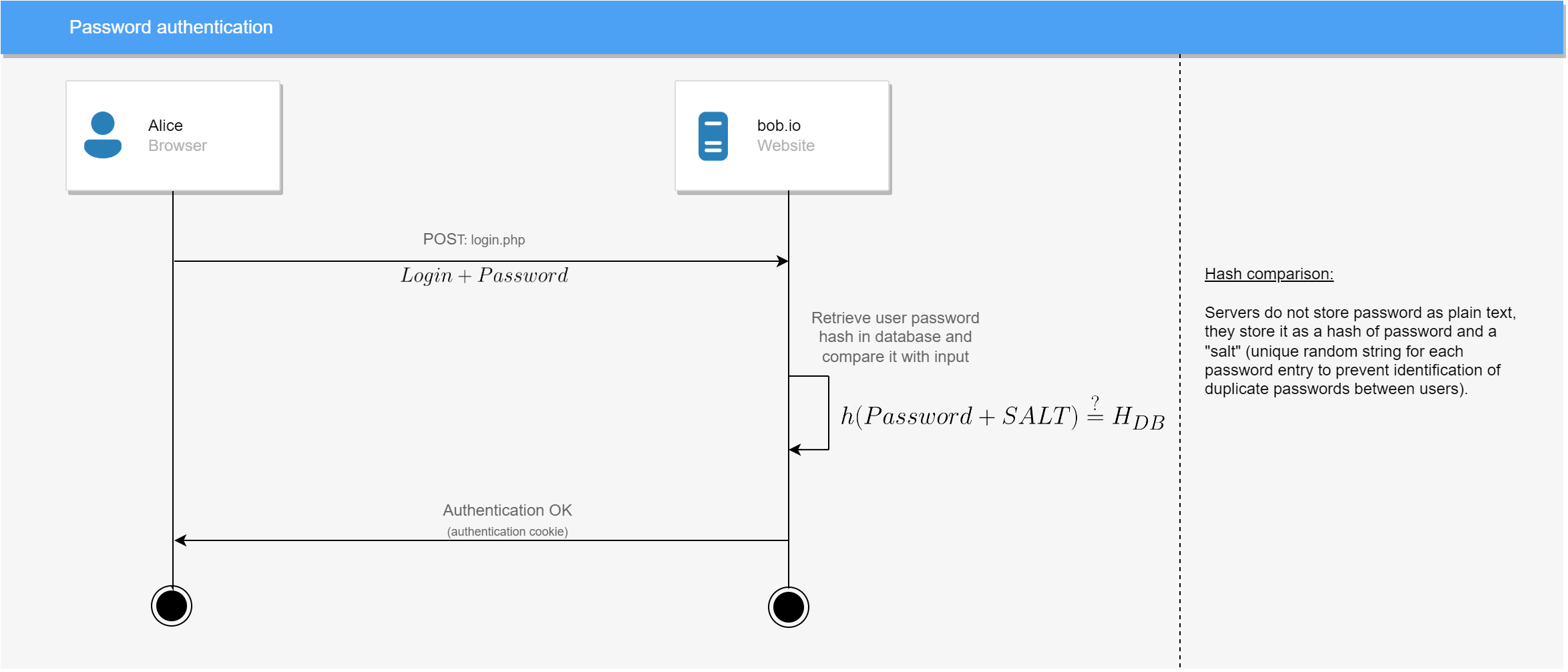
Password authentication
Scenario
Alice logged to https://bob.io using her password.
Prerequisites
- Alice must be registered on
bob.io
Diagram
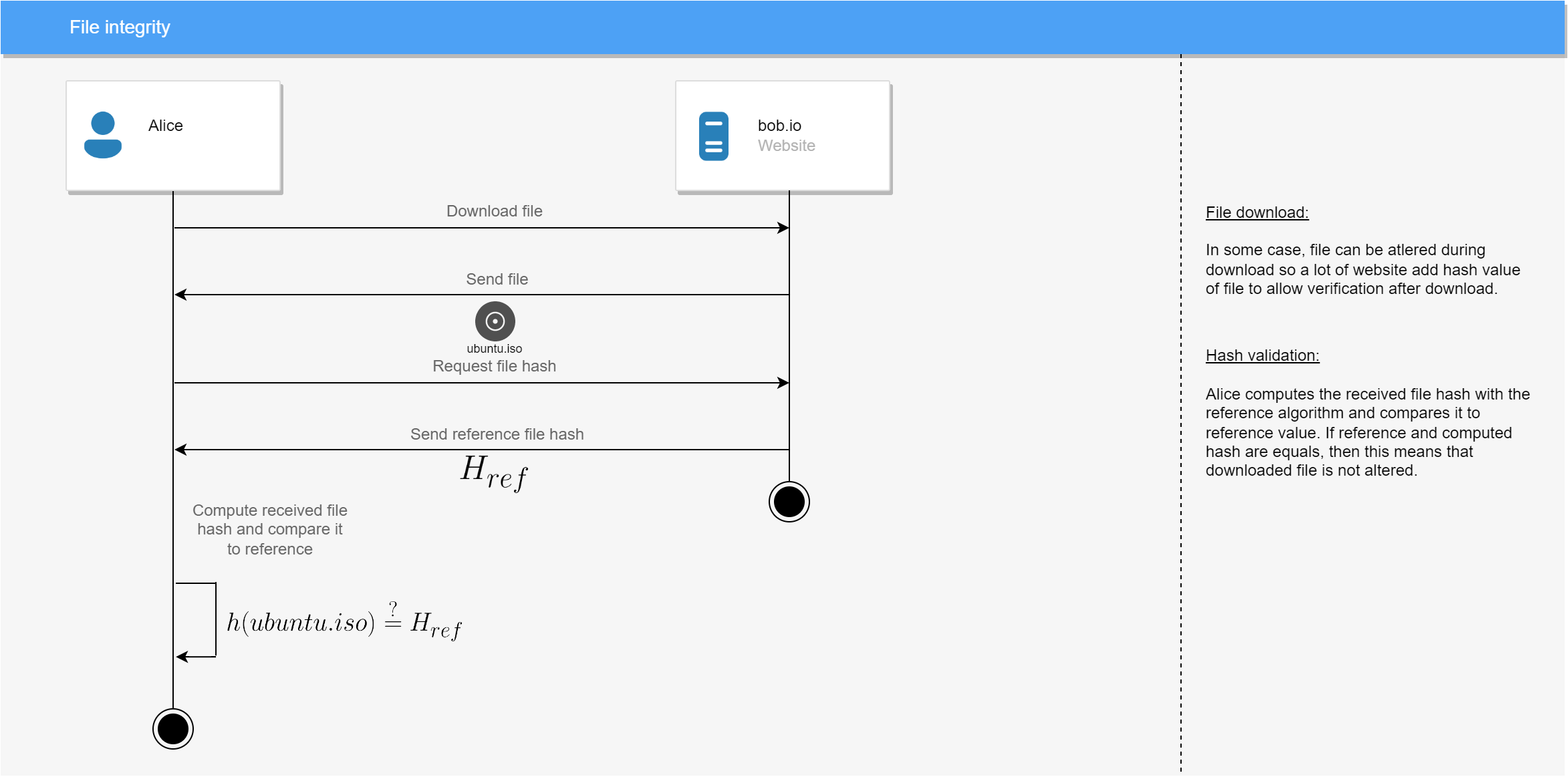
File integrity
Scenario
Alice downloads a file from https://bob.io and wants to verify the file integrity to make sure that the file was not altered during download.
Prerequisites
bob.iomust provide a hash values of files available for download (usually multiple values using multiple algorithms).
Diagram
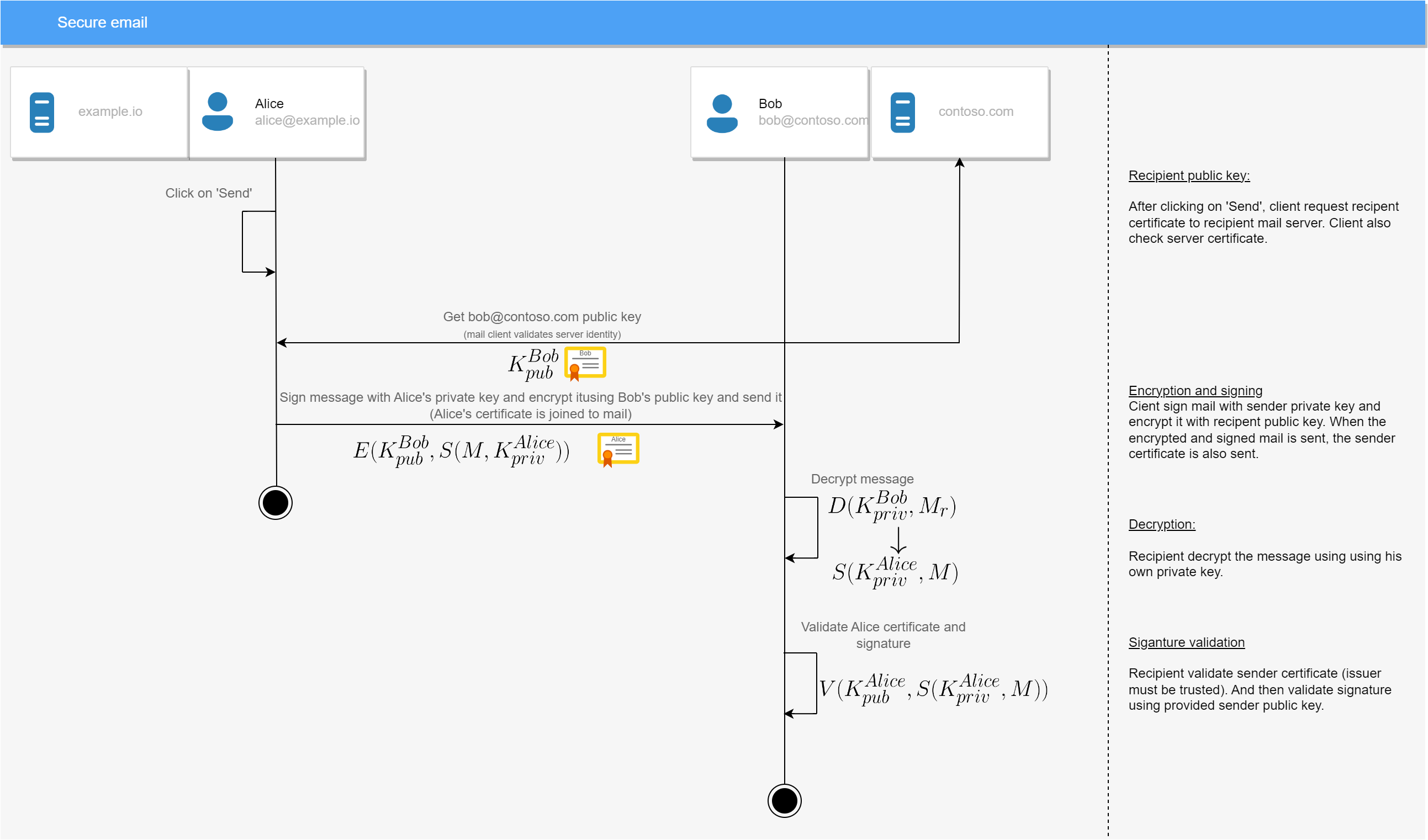
Mail signature (aka S/MIME)
Scenario
Alice sent a signed and encrypted mail to Bob (they don’t use the same mail server).
Prerequisites
- Bob and Alice must have their own certificate with private key issued by a certificate authority which is trusted by both (CAs can be different)
- Alice’s server must host Alice’s public key
- Bob’s server must host Bob’s public key
Diagram
Sources / usefull resources
- https://en.wikipedia.org/wiki/Alice_and_Bob
- https://en.wikipedia.org/wiki/RSA_
- https://www.devglan.com/online-tools/rsa-encryption-decryption
- https://en.wikipedia.org/wiki/Secure_Hash_Algorithms
- https://en.wikipedia.org/wiki/Transport_Layer_Security
- https://fr.wikipedia.org/wiki/Advanced_Encryption_Standard
- https://fr.wikipedia.org/wiki/X.509